First Primitives
Blockchains:
purpose of blockchain:
- the purpose of blockchain is to
have a network of computers agree on common state of data. consensusis a term used to mean a network coming into anagreement on state of data- using blockchain we can decentralize
where the code runsandagree on the output - there is no single owner of code’s execution. this doesnt mean some users don’t have higher permission over the code, i.e if you’re the program’s developer you can change the code. But, what we’re trying to convey here is
once the program is deployedit is going to run as programed. and that’s never gonna change. (code runs as programed) - code is transparently verifiable.
- blockchains are going to give us the garntee that the code we deployed is going to run the same as yesterday, today, and decades latter.
- the purpose of blockchain is to
Code decentralization
decentralization looks like this: you have
many machinesin anetwork, that are participating in anetwork. and we take the code and deploy it out tonetworkeachmachineis going have a copy of that code. And when the machines are called up on tovalidateor to run atransaction, they going to run it exactly the way it is going to run. And theBlockchainis going toenforcethat each machine is going to run the code exactly the way it was written.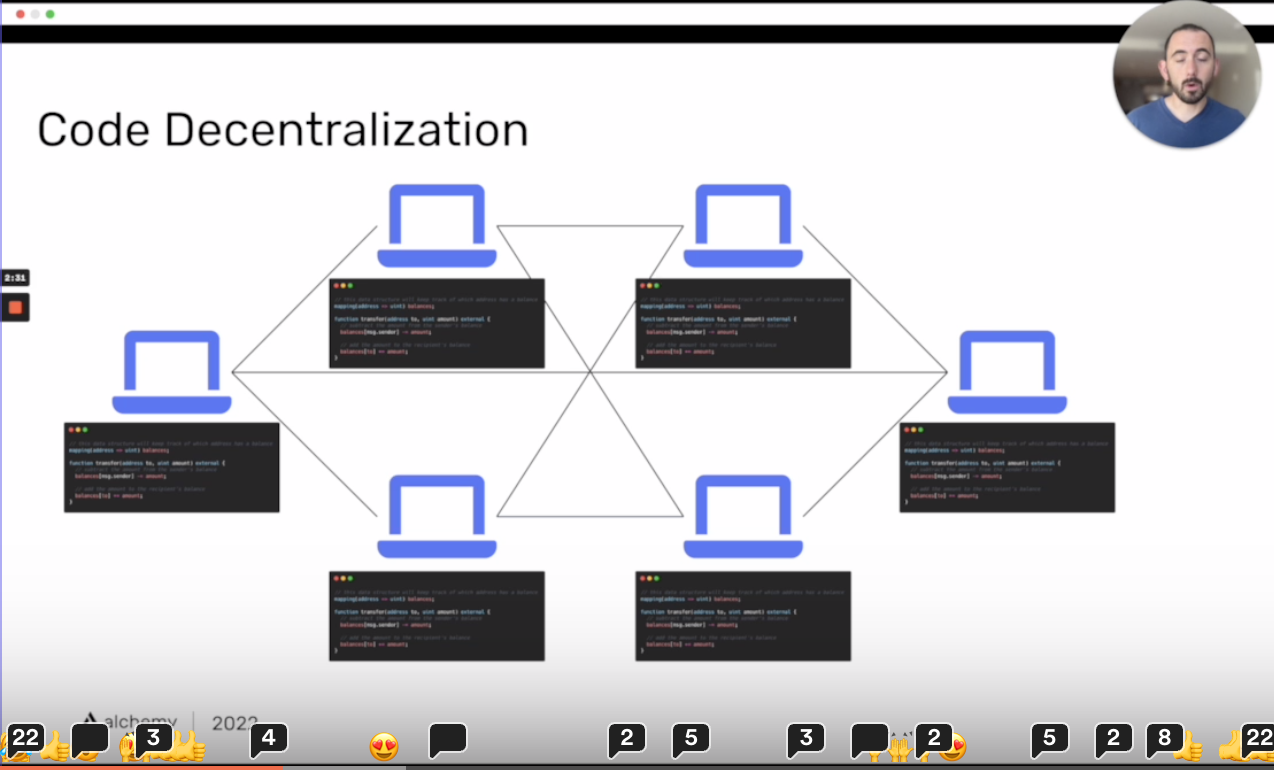
Blockchain Network
Blockchainis aprotocolconnecting all themachinesornode- each
machineornodewill run the code as written. - the blockchain
enforcestheserules(i.e all machines running the code as is) and because the blockchain isenforcingthese rules it is calledsmart contracts
Common usecases of blockchain
ex: in cryptocurrency: we have 3 people and they want send each other some money. So, how would they trust each other they’re not fooling any one?
trust? Bitcoin first came up with foolproof system allows people exchange value using pear to pear network.blockchain is created to solve trust
Smart contract blockchains
smart contract blockchainsprovide developers a way todecentralize where the code runsone important thing to drill home is-decentralization isn't about the code itselfbuthow the code is executed
Bitcoin
- bitcoin is the
first successfull blockchain. - it is not the first interms of being there,
there were many researches and attempts before bitcoin. - bitcoin is the first to put all of these
cryptographic primitivestogether in such a way to actually create a blockchain could continue to work and function. - and many components were already discovered, and it was bitcoin first to assemble those components to get a functioning blockchain.
Components of decenteralization
- taking these components together and supplying them with a network of machines is what is going to make decentralization emerge.
Security- proof of work (bitcoin)FinancialIncentives: mining rewards(bitcoin)Authentication: public key cryptography(i think this common among other networks)Chronology: Linked data structure(i think is common as well)Permissionless: peer to pear network (common among others as well)
All of these 5 components work together to emerge a decentralization.
Crypto
- Long before
cryptocurrencythere wascrypto - today u may hear crypto being used to refer a
crytocurrency. butcryptois sth that was researched long beforecryptocurrency. - These
crytopgraphic primitiveslike :Crytopgraphic HashesandPublic Key crytographywere discovered in the1970s
Cryptographic Hashes
- before that let’s see what
hash functionis.
Hash function
is like give me some
input,big or smalland I will give you afixed size output. Thesize of outputdepends on thetype of hash algorithm.input can be any type of data:
number,string,image,video…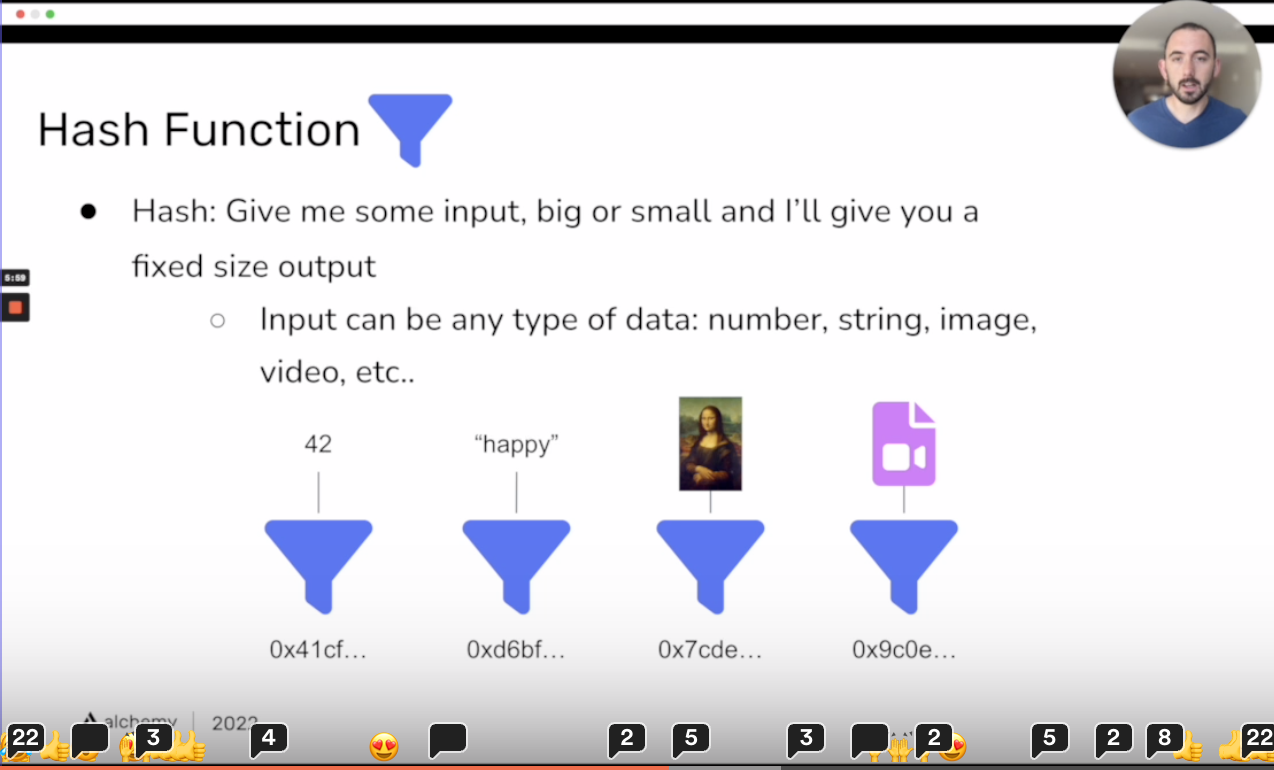
the
hash algorithmwe’re going to focus for now isSHA256SHA256is acryptographic hash function.and it provides256 bitoutput.a
crytopgraphic hash functionis a function thatdemonestratesthese properties:deterministicpseudorandomone-wayfast to computecollision resistant
Deterministic:- i.e the
same inputtocryptographic hash functionis going to result thesame output. - imagine we can put any data we want.
- so, the
outputof acryptographic hash functionis going to be the representative of thedata we inputi.e this is really big because we now can put something really really big and represent it with smaller data. AWESOME!
- i.e the
Pseudorandom:- unpredictable! you have no clue! You cannot get it by putting similar inputs.
One-way:- given an
outputI cannotpredictwhat the input was. - the only way you could do it by repeatedly guessing.
SHA256has a256bit result and i can say our not gonna ever get it my boi.
- given an
Fast-to-Compute:- should be fast to compute on a modern computer
Collision Resistant:- having 2 inputs they SHOULD NOT create the same
output. - but the chances of these 2 input creating the same
outputis possible, but the chances are soooo small because of huge address base2**256(we can neglect the possibility)
- having 2 inputs they SHOULD NOT create the same
2 important usecases of Hash functions
commitments:- we use
hash functionfor itscommitmentproperty in protocol design and smart contract design. - for ex: we can pass an image monalisa to
hash functionand we can commit to thatoutput dataas monalisa.
- we use
proof of work- absolutely insturmental for proof of work mechanism!
exercise: Burteforce Hashing
you
bruteforceto guess theinputfrom the a givenoutput. Or you can use aRainbow tableto determine the input form theoutput.What’s
Rainbow table?- rainbow table is
precomputedtable that contains alarge number of possible passwordsandtheir corresponding hash values. It is used to quicklyreverse engineer a hashed password by looking up its corresponding original passwordin the table.
- rainbow table is
For securitypurposes it is important to use randomsaltwhich you can add to yourinputto make it unguessable using the methods above.How does using a
random saltlower chance of password being guessed usingrainbow table?- So, using random salt means adding a unique string to the password before hashing process. So, say 2 users have the same password, (ex: “password”), so, when using salt you add a unique text. maybe for the first user
it was likepasswordLdks23&32and for second user it is likepasswordEI#)@, then we start the hashing process after adding a random salt. Resulting a different hash value for the same password. This gonna make usingRainbowTablesuper ineffective, time-consuming, much more challenging for guessing or revers engineer.
- So, using random salt means adding a unique string to the password before hashing process. So, say 2 users have the same password, (ex: “password”), so, when using salt you add a unique text. maybe for the first user
What does
reverse engineeringmean?- is process of studying and analyzing a product, system or technology in order to
understand how it works or was designed. often used togain insights into existing technology,replicateormodify it, oridentify potential vulnerabilityorweakness.
- is process of studying and analyzing a product, system or technology in order to
TASK 1: Find Favorite Color
Brute Force Hashing
Cryptographic Hash Functions like SHA256 are one-way functions. This means that if you have the input, it’s relatively trivial to find the output. On the other hand, if you have the output, it is infeasible to find the input.
However, if you knew the hashes of some common inputs, then you could brute-force guess at the output or create a Rainbow Table to determine what that input is.
It’s easy to find that the SHA256 hash of “apples” is 0xf5903f…0f74d9. If this was a likely input, a hacker could search for it specifically and know that the input was “apples”! 😱
⚠️ For security purposes, it’s important to remember to use a random salt which you can add to your input to make it unguessable via the methods mentioned above!
🏁 Your Goal: Find the Color
Given a SHA256 hash, find the color input that would generate that hash. You can assume that all the hashes be generated only from colors provided in the COLORS array.
To take the hash of a color, first use utf8ToBytes to translate the string to bytes. Then, use sha256 to hash it.
When you want to compare two hashes, first use toHex to turn each hash from a Uint8Array to a string of hexadecimal characters.
So comparing two hashes would look like this:
1 | const a = 'apple'; |
Wondering what utf8 stands for? The UTF-8 standard translates all the possible keyboard characters you can think of into bytes. This is an agreed upon standard to ensure we all get the same bit values representing the letters and words we see on the screen. Learn more about utf8 here.
Details:
Rainbow Table
A rainbow table is simply a table which maps common inputs to their hash output. For instance, we could map common passwords to their SHA256 hashes:
COMMON PASSWORDS SHA256 HASH
password 0x5e8848…1542d8
qwerty 0x65e84b…2337c5
111111 0xbcb15f…09802a
12345678 0xef797c…98a64f
abc123 0x6ca13d…118090
Even though the password should be unguessable, given a hash output, these common passwords make it easy to create a rainbow table to find what the plaintext input would be.
⚠️ If a company were to lose their database of passwords (which happens way too often) and they do not protect their password hashes with a salt, it may be relatively easy for a hacker to use a rainbow table to find which passwords you use. From there, they can try those passwords on other services.
My solution:
1 | const { sha256 } = require('ethereum-cryptography/sha256'); |
Test to run against:
1 | const { assert } = require('chai'); |